Microsoft Teams
Microsoft Office 365 applications including Microsoft SharePoint and Microsoft Teams use Azure Active Directory to authenticate users.
Microsoft Teams allows Guest users to be added to a Team.
Azure Active Directory is used to support the Teams Guest user feature.
In the screenshot below John Doe with email address john@doe.com is added as a Guest user.
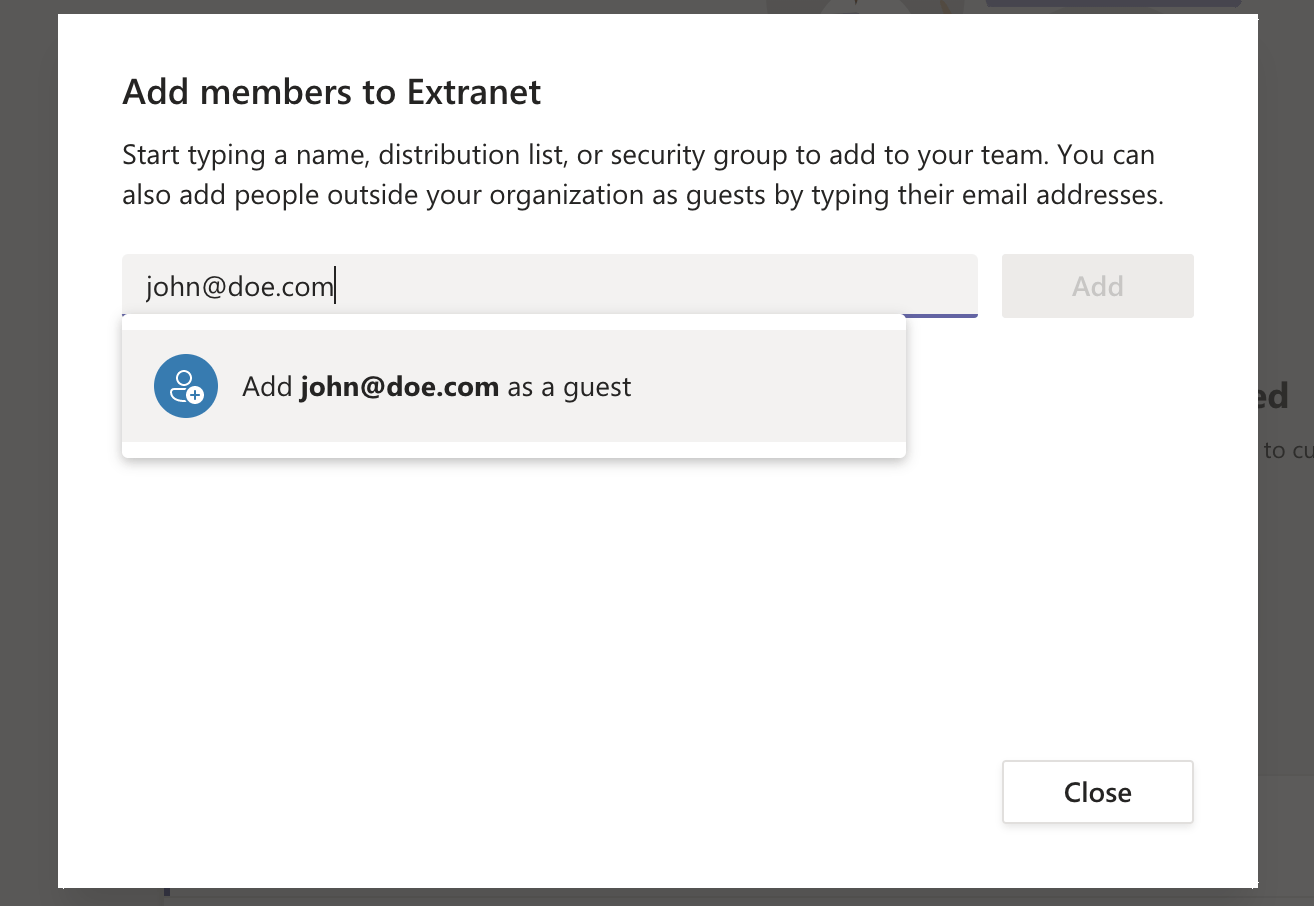
John Doe is being added as a Guest user.
Members and guests
Once John Doe has been added to the Team his account is included in the "Members and guests" list.
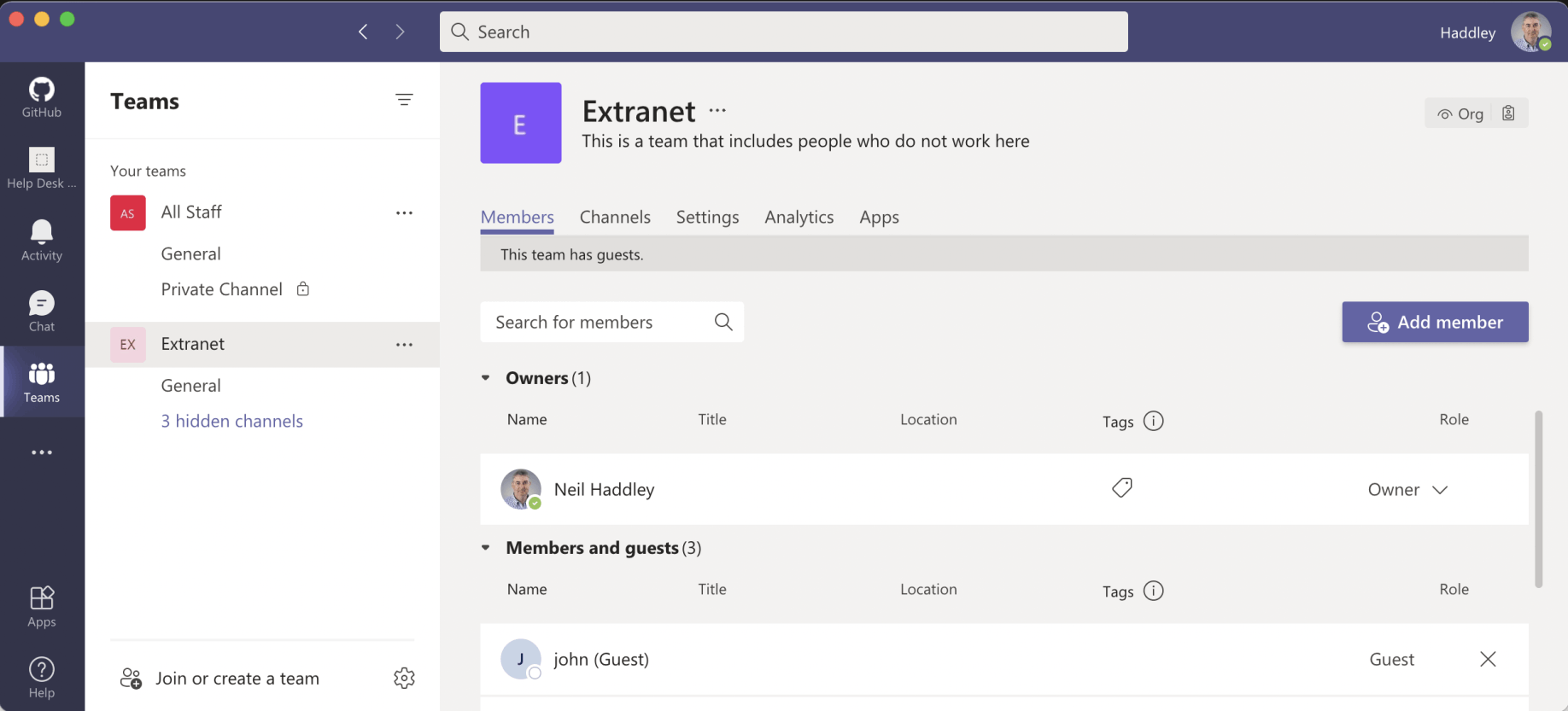
John has been added as a (guest) member of the Team
Azure Active Directory Users
Switching to the Azure Portal we can see that an external (EXT) Active Directory account has been added for John Doe.
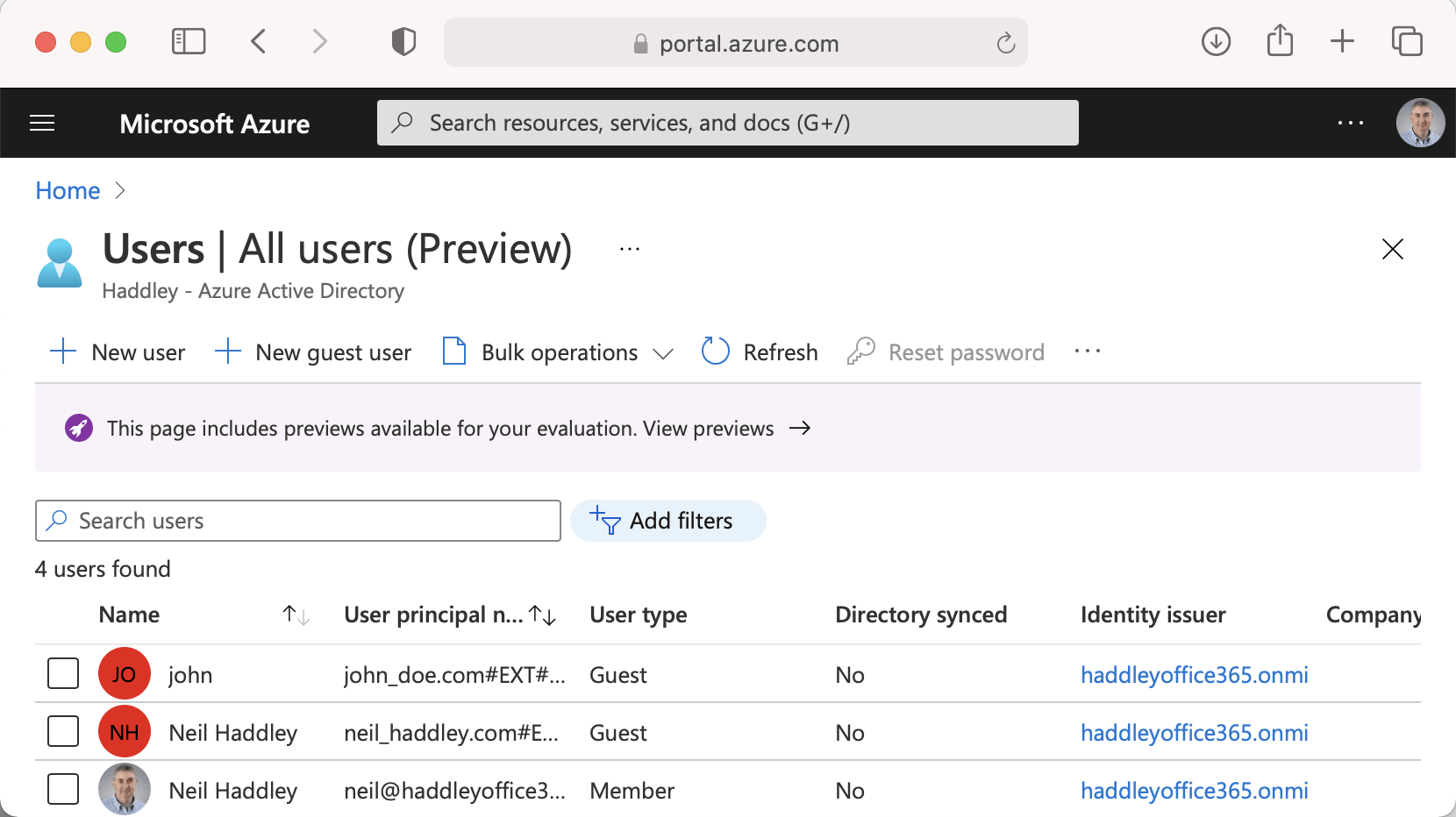
Azure Active Directory Users
Custom Web Application
We can use the same Azure Active Directory user list to authenticate users accessing a custom "Who am I" web application.
App Registration
The key step is the creation of an "application registration".
Navigate to the Azure Active Directory service and select App registrations page.
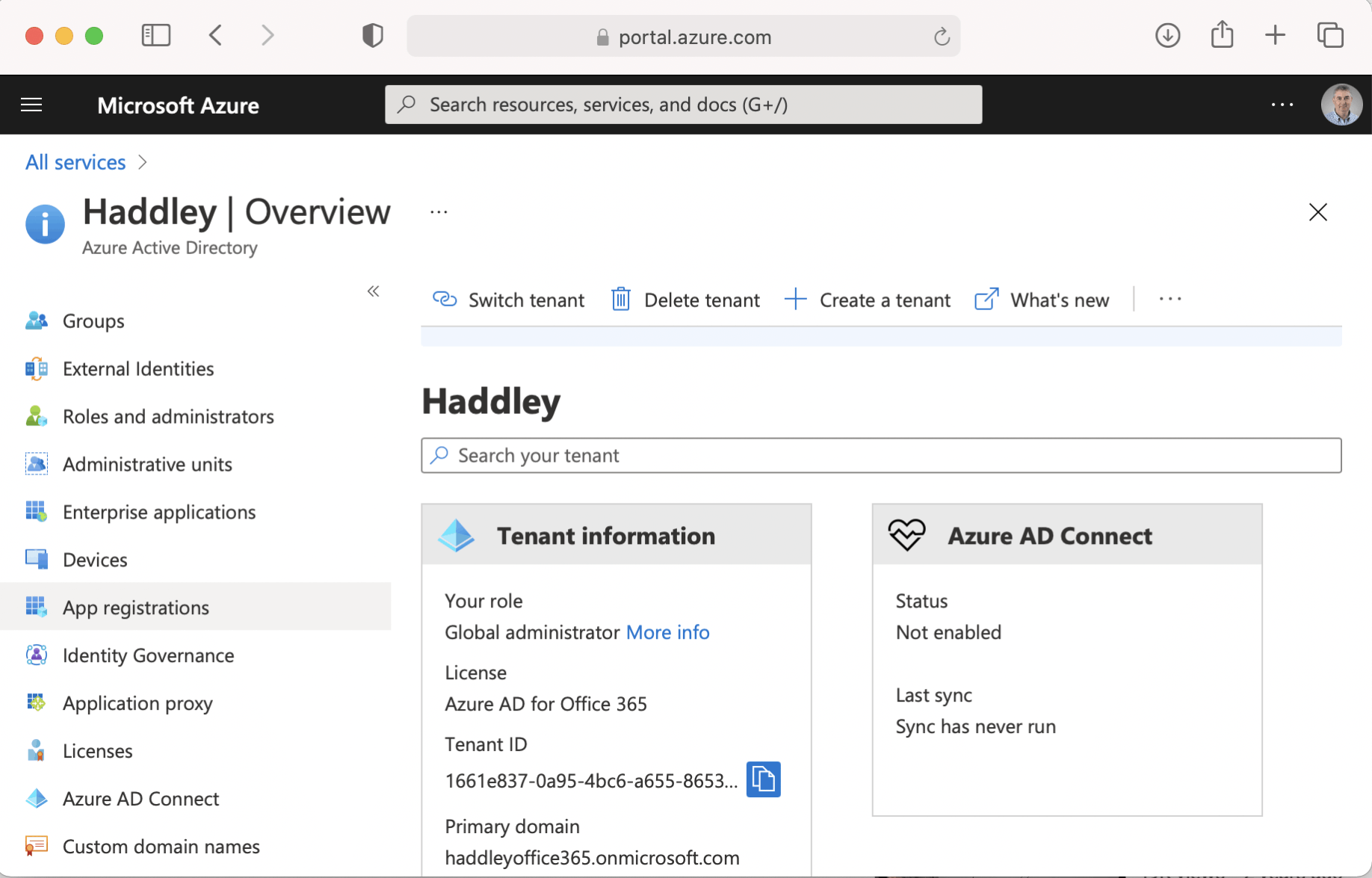
Navigate to Azure Active Directory and select App registrations
Click the "+ New registration" button
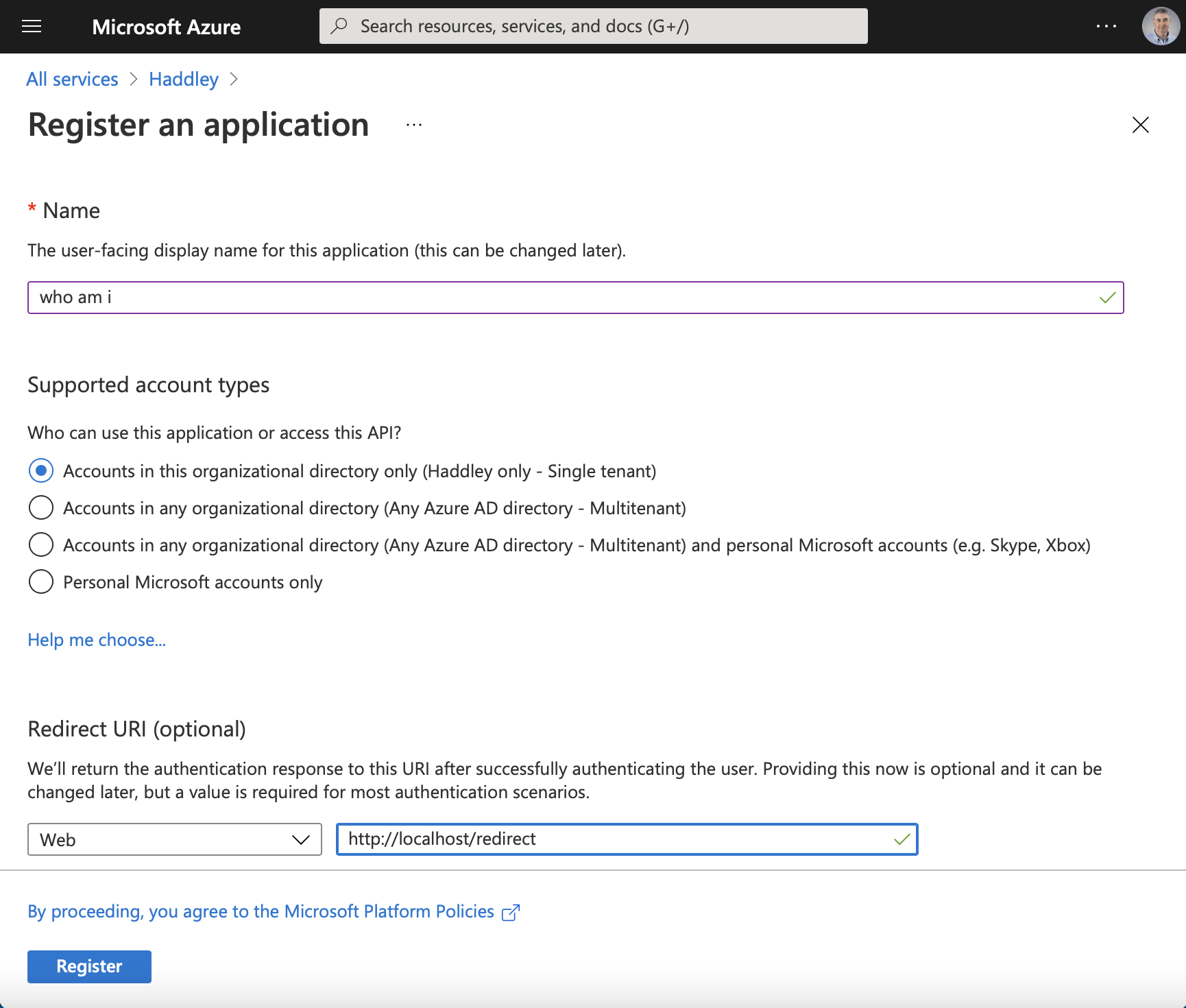
Enter the user-facing display name "who am i" in this case.Enter the redirect uri (this is the address the user will be directed to once they have successfully entered their credentials).
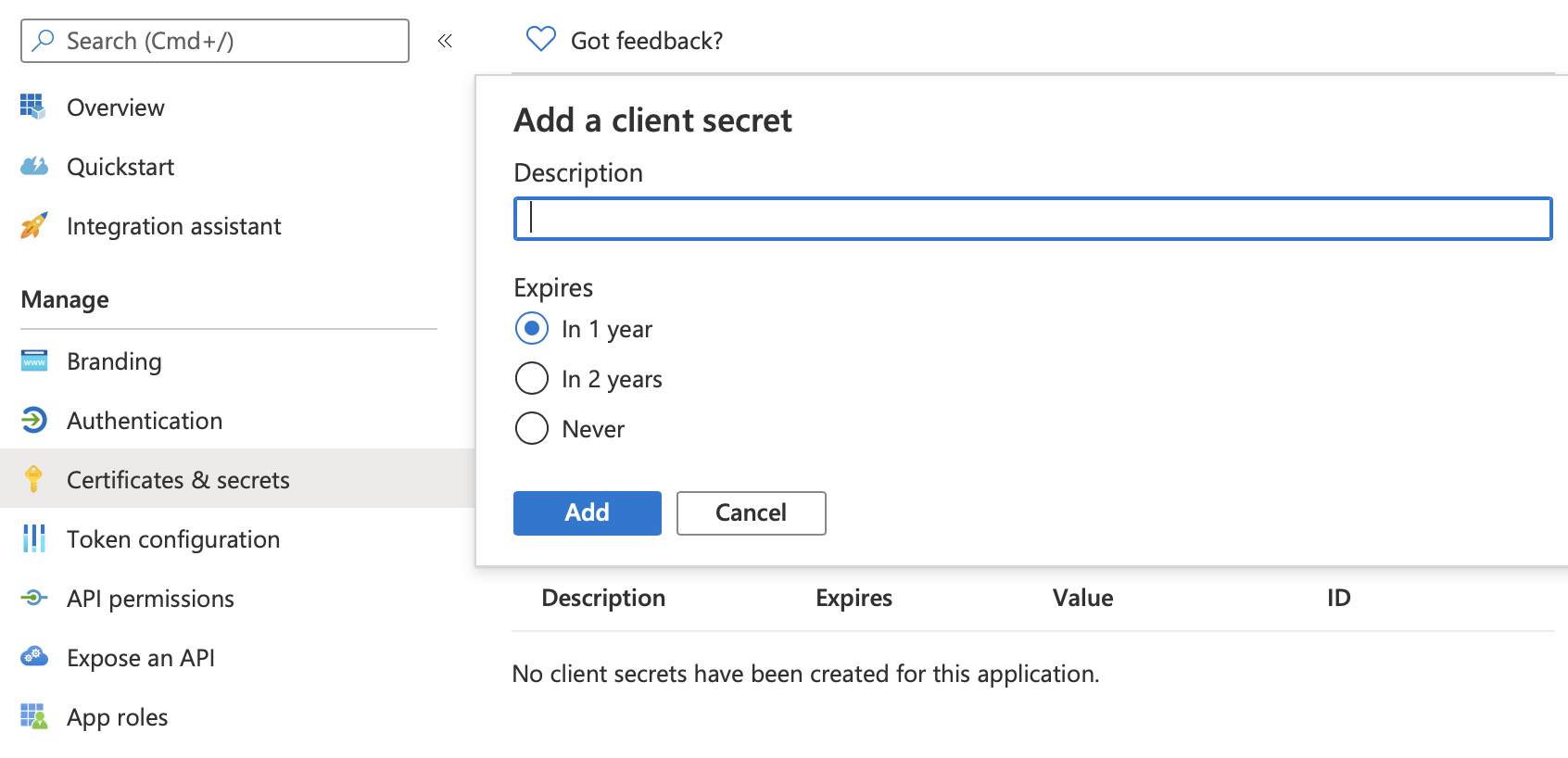
We need to create a client secret
We need to take a note of these three values
Application (client) ID 63fe01c7-f396-484e-8a48-760f
Directory (tenant) ID 1661e837-0a95-4bc6-a655-8653
Client secret -~nGgWS3F7y~-o2etNGc0BW_ik_*
Test the solution
To test the who-am-i web application we can navigate to http://localhost:3000
We attempt to navigate to http://localhost:3000
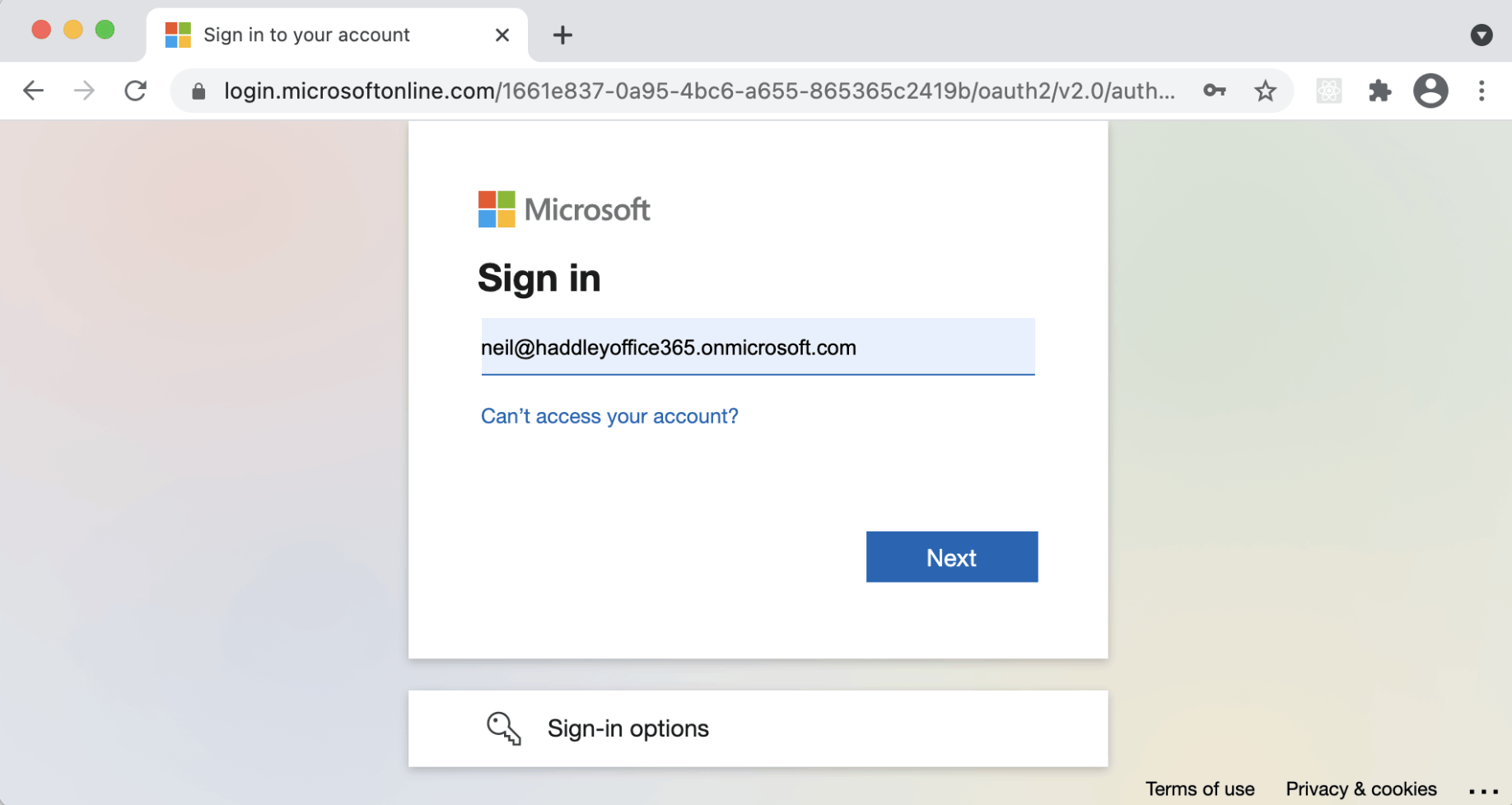
We are redirected to the Azure Active Directory Sign in page (unless federated identity management is enabled).
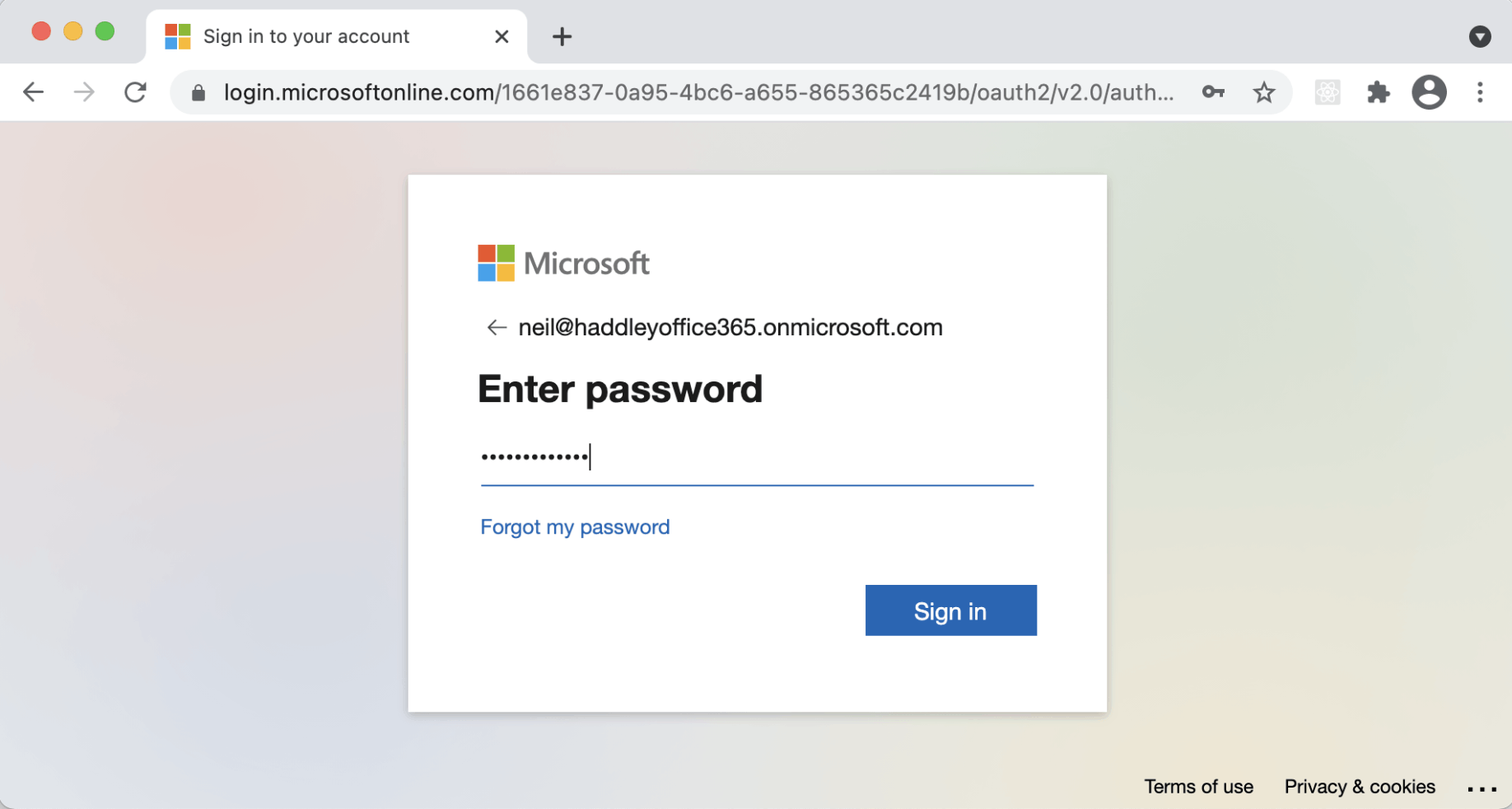
Once we have entered a correct email/username and password...
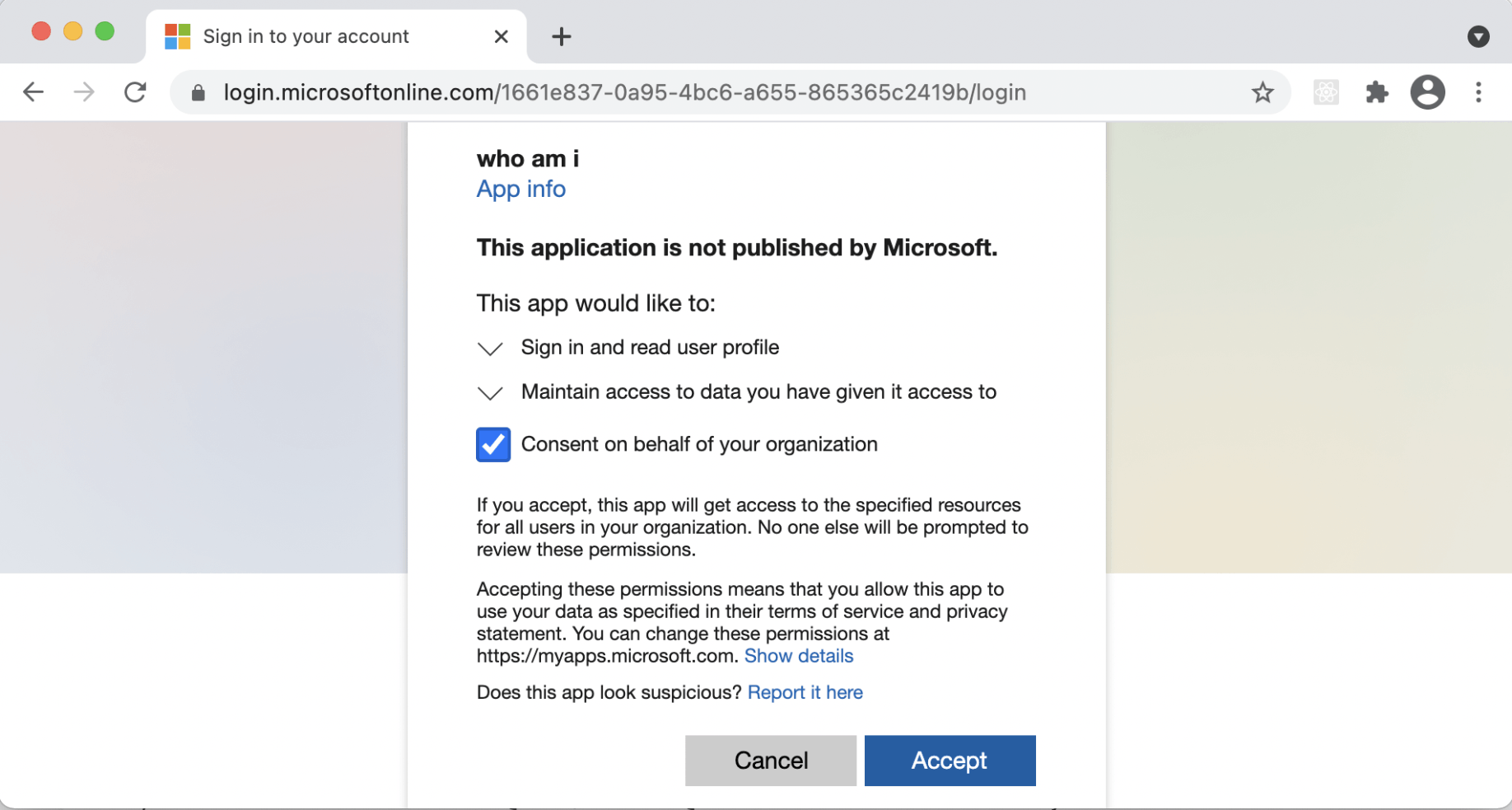
...we are asked consent to having our personal details passed to the "who am i" application (unless two factor authentication is enabled).
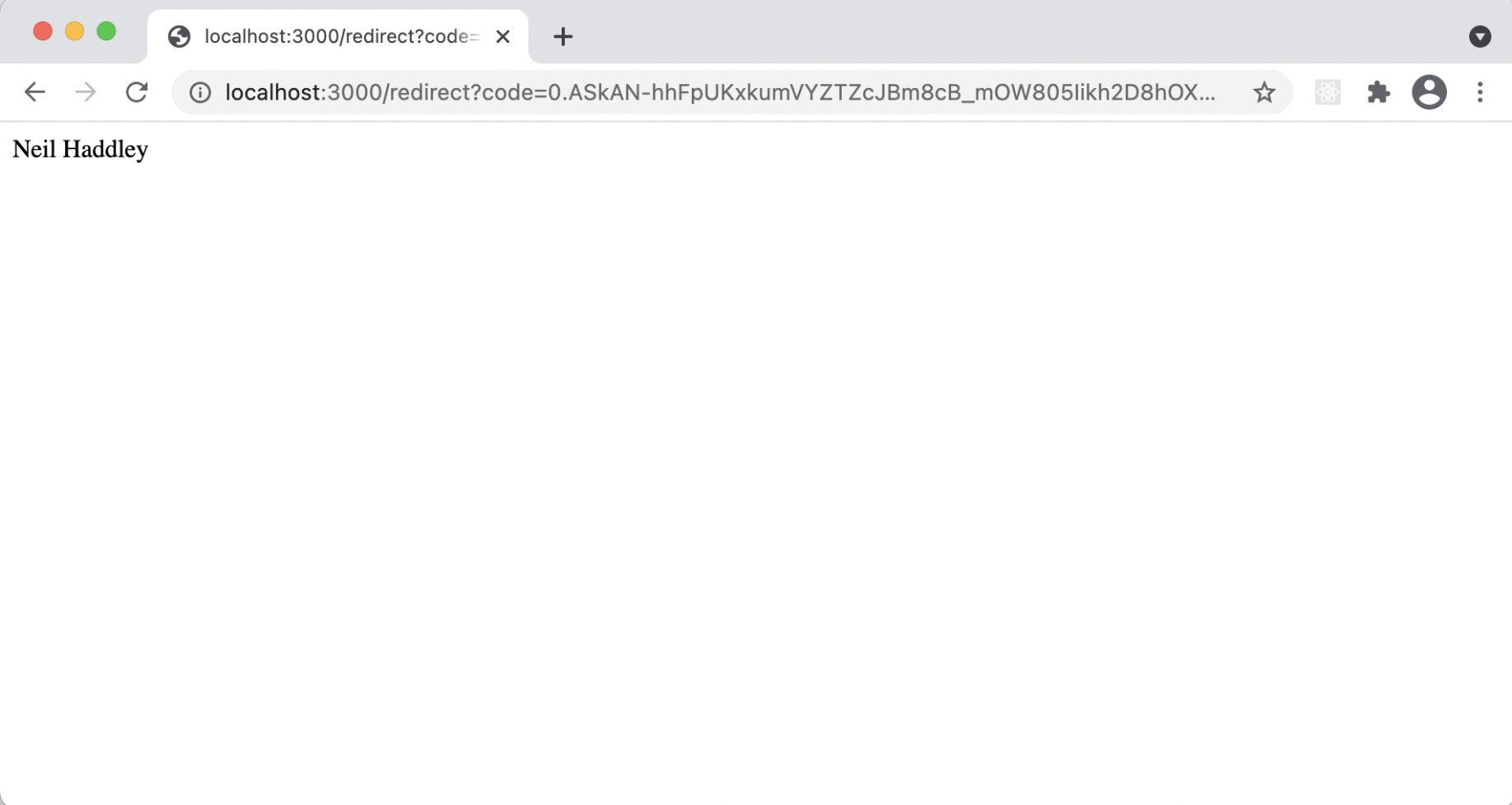
In this case we are redirected to "/redirect" and the name of the authenticated user is displayed
package.json
TEXT
1{ 2 "name": "who-am-i", 3 "version": "1.0.0", 4 "description": "", 5 "main": "index.js", 6 "dependencies": { 7 "@azure/msal-node": "^1.0.0", 8 "express": "^4.17.1", 9 "uuid": "^8.3.1" 10 }, 11 "devDependencies": {}, 12 "scripts": { 13 "start": "node index.js" 14 }, 15 "repository": { 16 "type": "git", 17 "url": "git+https://github.com/Haddley/who-am-i.git" 18 }, 19 "author": "", 20 "license": "ISC", 21 "bugs": { 22 "url": "https://github.com/Haddley/who-am-i/issues" 23 }, 24 "homepage": "https://github.com/Haddley/who-am-i#readme" 25}
index.js
TEXT
1/* 2 * Copyright (c) Microsoft Corporation. All rights reserved. 3 * Licensed under the MIT License. 4 */ 5const express = require("express"); 6const msal = require('@azure/msal-node'); 7 8const SERVER_PORT = process.env.PORT || 3000; 9const REDIRECT_URI = "http://localhost:3000/redirect"; 10 11// Before running the sample, you will need to replace the values in the config, 12// including the clientSecret 13const config = { 14 auth: { 15 clientId: "63fe01c7-f396-484e-8a48-760f********", 16 authority: "https://login.microsoftonline.com/1661e837-0a95-4bc6-a655-8653********", 17 clientSecret: "-~nGgWS3F7y~-o2etNGc0BW_ik_*******" 18 }, 19 system: { 20 loggerOptions: { 21 loggerCallback(loglevel, message, containsPii) { 22 console.log(message); 23 }, 24 piiLoggingEnabled: false, 25 logLevel: msal.LogLevel.Verbose, 26 } 27 } 28}; 29 30// Create msal application object 31const pca = new msal.ConfidentialClientApplication(config); 32 33// Create Express App and Routes 34const app = express(); 35 36app.get('/', (req, res) => { 37 const authCodeUrlParameters = { 38 scopes: ["user.read"], 39 redirectUri: REDIRECT_URI, 40 }; 41 42 // get url to sign user in and consent to scopes needed for application 43 pca.getAuthCodeUrl(authCodeUrlParameters).then((response) => { 44 res.redirect(response); 45 }).catch((error) => console.log(JSON.stringify(error))); 46}); 47 48app.get('/redirect', (req, res) => { 49 const tokenRequest = { 50 code: req.query.code, 51 scopes: ["user.read"], 52 redirectUri: REDIRECT_URI, 53 }; 54 55 pca.acquireTokenByCode(tokenRequest).then((response) => { 56 console.log("\nResponse: \n:", response); 57 // Return the current user's name 58 console.log(response.account.name); 59 res.send(response.account.name); 60 res.sendStatus(200); 61 }).catch((error) => { 62 console.log(error); 63 res.status(500).send(error); 64 }); 65}); 66 67 68app.listen(SERVER_PORT, () => console.log(`Msal Node Auth Code Sample app listening on port ${SERVER_PORT}!`))